Learn how to manage the authentication cache in SQL Server using the DBCC FLUSHAUTHCACHE command. With step-by-step instructions and frequently asked questions, this thorough book covers its background, advantages, and potential downsides.
Table of Contents
Introduction
Maintaining vigilance against unauthorized access is essential for database security. The DBCC FLUSHAUTHCACHE command from SQL Server is used to maintain the authentication cache and strengthen security measures. Although this command appears to be a straightforward tool, it has a significant influence on preventing unauthorized access. We explore the history, benefits, and drawbacks of DBCC FLUSHAUTHCACHE in this book so that you may be well-equipped to use it efficiently and strengthen your SQL Server’s defense against possible attacks.
A Historical Perspective: Unveiling DBCC FLUSHAUTHCACHE
DBCC FLUSHAUTHCACHE has its origins in prior iterations of SQL Server. It was first designed as a safety precaution to delete the authentication cache, but it was eventually developed to improve user authentication and provide protection from potential vulnerabilities.
You may also like : DBCC UPDATEUSAGE: Using SQL Server Storage Management to Its Fullest Potential
Advantages of this DBCC Command
Advantages of DBCC FLUSHAUTHCACHE are given below:
1. Removing Unauthorised Access
This DBCC Command clears the authentication cache, invalidating any credentials that may have been stored there. This preventative precaution is taken to prevent access by unauthorized users.
2. Immediate Effect
The command takes effect right away. Users are prevented from abusing stored credentials by a quick clearing of any cached authentication tokens.
3. Enhanced Security
This DBCC Command fortifies your SQL Server against potential security breaches by deleting cached authentication data and reducing the window of exposure.
Disadvantages of this DBCC Command
Disadvantages of DBCC FLUSHAUTHCACHE are given below:
1. Impact on Performance
Although it won’t have much of an effect, running this DBCC command may cause a tiny performance hit while the authentication cache is emptied and rebuilt for authorized users.
2. Users who have logged out
Any user who is presently authenticated using credentials that have been cached will be required to reauthenticate, which might be annoying.
You may also like : Unveiling the Power of DBCC FREEPROCCACHE: A Comprehensive Guide
3. Security Points to Remember
Applying new security settings or permissions may benefit from deleting the authentication cache, but doing it often may conceal underlying security setup problems. When employed as a band-aid solution instead of addressing the underlying source of authentication issues, it can provide the impression that security is being restored.
For instance:
It is possible to create misconfigurations and security vulnerabilities by relying on DBCC FLUSHAUTHCACHE to enforce security changes rather than correctly specifying security settings.
4. Effect on Systems with High Availability
Clearing the authentication cache can have more significant effects on high-availability systems, such as those that use clustered environments or Always Availability Groups. Potential inconsistencies or failover delays may result from its impact on the synchronization and failover operations.
For instance:
Because every node must re-authenticate users, using DBCC FLUSHAUTHCACHE in a clustered environment may cause delays in the failover process, which may affect the high-availability strategy as a whole.
5. Higher Latency for Authentication
Following the execution of DBCC FLUSHAUTHCACHE, every authentication request needs to be handled from the beginning. The need for a complete authentication cycle for every connection may cause latency, which is particularly apparent in settings with heavy traffic.
For instance:
The extra time required for each authentication can pile up in a system where many users log in often, causing noticeable delays.
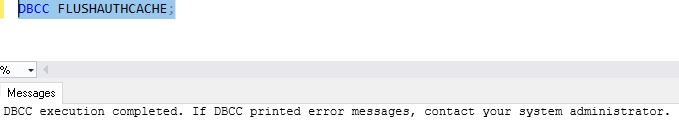
Syntax
DBCC FLUSHAUTHCACHE;Permissions Required to Execute this DBCC Command
Having the ALTER ANY CONNECTION privilege or being a member of the administrator fixed server role are prerequisites for running this DBCC command. These permissions make sure that only people with the proper authorization may carry out the command.
Examples: Using DBCC FLUSHAUTHCACHE to Its Full Potential
1. Immediate Security Enhancement
Execute this DBCC command to swiftly empty the authentication cache and stop unauthorized access. Immediate Security Enhancement.
DBCC FLUSHAUTHCACHE;
2. Scheduled Security Maintenance
To guarantee continuing defense against possible vulnerabilities, schedule regular executions of this DBCC command.
You may also like : Understanding Indexes in SQL Server: A Complete & Comprehensive Guide
Conclusion
Vigilance against unauthorized access is crucial in the changing world of database security. Your defense toolbox should include this DBCC command to make sure that cached credentials don’t turn into vulnerabilities that may be exploited. Understanding its benefits, drawbacks, and execution needs will enable you to proactively improve the security posture of your SQL Server. Make intelligent use of DBCC FLUSHAUTHCACHE to protect your database from security weaknesses, secure your data, and uphold user confidence.
Frequently Asked Questions (FAQs)
Q: Does this DBCC command impact users that are presently logged in?
Ans: Yes, running this DBCC command requires reauthentication from logged-in users.
Q: Is this DBCC command capable of causing downtime?
Ans: No, running the command has little effect on performance and doesn’t shut down the server.
Q: How frequently should I run the security tool this DBCC command?
Ans: Depending on your security policy, you might want to execute it on a regular basis to make sure the authentication cache is kept clear.
Q: Can this DBCC command have an effect on running applications?
Ans: Although minor, a performance impact could exist. Consider running the command when there is less traffic.
Q: A mirrored database may use this DBCC command, right?
Ans: You may use mirrored databases to run it. But take into account any potential effects on failover circumstances.
Q: Can access be revoked for a specific user using this DBCC command?
Ans: The whole authentication cache is cleared by DBCC FLUSHAUTHCACHE, which has an impact on all users. It is not intended for the cancellation of access for specific users.
Q: Do application connections become affected by this DBCC command?
Ans: Yes, running this DBCC command can affect programmes that use credentials that have been cached. Users can see brief reauthentication requests.
Q: Does this DBCC command also have an impact on Windows Authentication?
Ans: Yes, this DBCC command clears the cached credentials for both Windows Authentication and SQL Server, boosting overall security.
Q: How do high availability scenarios like AlwaysOn Availability Groups affect this DBCC command?
Ans: When a failover occurs, using this DBCC command in high-availability systems may result in reauthentication requests. Think about how it could affect user experience.
Q: Can replicated databases be used to perform this DBCC command?
Ans: Yes, replicated databases may utilize this DBCC command. However, pay close attention to how it affects user connections and replication procedures.
Q: Does this DBCC command affect execution plans that have been cached?
Ans: No, the this DBCC command just clears cached authentication tokens; it does not affect how queries are executed.
Q: After being used, can this DBCC command be undone?
Ans: No, the cache is emptied and cannot be restored once this DBCC command has been run. The necessity for users to re-authenticate.
Q: Does running this DBCC command need any downtime?
Ans: No, this DBCC command may be run without shutting down the server. However, take user reauthentication into account.
Q: How do application connection pools and this DBCC command interact?
Ans: Running this DBCC command can cause apps that use connection pools to alert the user for reauthentication, which would be annoying.
Q: Do you have a suggested schedule for utilizing this DBCC command?
Ans: The frequency is determined by your security procedures and any dangers. To keep your authentication cache clean, think about running it frequently.
See Also :
SQL Server Configuration Manager
Dynamic Data Masking in SQL Server
DBCC SQLPerf (LogSpace):Top 15 Usage
A Powerful SQL Server Developer Edition
Deadlocks in SQL Server : Understanding and Resolving Database Concurrency Issues

